
Cyber-attacks have become sophisticated and frequent – with AI allowing them to automate breach attempts. Many organizations exploit cloud and IoT technology to expand their digital operations, but the downside is that this expansion augments network complexity and the attack surface further. As new technology booms, cybercriminals adapt and discover new hacking techniques to apprehend sensitive data. AI and IoT have the capability to revolutionize the world, but what if these new technologies are weaponized by cybercriminals and how can one save themselves from attacks but still use the technologies?

How are IoT devices targeted?
Before IoT attackers even attempt cyberattacks on an IoT device, they quite often study the device to identify vulnerabilities. This is generally done by buying a carbon copy of the IoT device they are targeting from the market. They then reverse engineer the device to devise a test attack to see what turnout can be acquired and what avenues exist to attack the device.
A physical attack is a low-tech type of attack where the hardware of the target device is exploited to the benefit of the attacker. However, its power system may become overloaded and require replacement, when an IoT device is connected to a high voltage power source.

IoT devices tend to be more vulnerable to Man-in-the-Middle(MITM) attacks as there’s an absence of standard implementations to fight the attacks. There are two typical modes of MITM attacks: cloud polling and direct connection. The smart home device constantly communicates with the cloud, generally to look for firmware updates. Attackers can deflect network traffic using Address Resolution Protocol (ARP)* poisoning or by altering Domain Name System (DNS)* settings or intercept HTTPS traffic by using self-signed certificates or tools such as (Secure Sockets Layer) SSL. IoT devices do not verify the authenticity of the trust level of certificates, making the self-signed certificate method particularly effective. In the case of direct connections, devices communicate with a hub or application in the same network. By doing this, mobile apps can locate new devices by probing every IP address on the local network for a specific port. An attacker can do the same thing to discover devices on the network.
The most predominant form of MITM attack leveraged against IoT devices is Bluetooth connection. Generally, IoT devices run Bluetooth Low Energy (BLE), are designed with IoT devices in mind to be smaller, cheaper, and more power-efficient. BLE uses three-phase pairing processes: first, the initiating device sends a pairing request, and the devices exchange pairing capabilities over an insecure channel; second, the devices exchange temporary keys and verify that they are using the same temporary key, which is then used to generate a short-term key. third, the created key is exchanged over a secure connection and can be used to encrypt data.
There are three common pairing methods popular with IoT devices: i) JustWorks ii) Passkey iii) Out-of-Band pairing. Out of the above three paring methods, the most insecure one is JustWork as it always sets the temporary key to 0. To perform MITM attacks in BLE networks, the attacker must use two connected BLE devices himself: one device acting as the IoT device to connect to the target mobile app, and a fake mobile app to connect to the target IoT device.
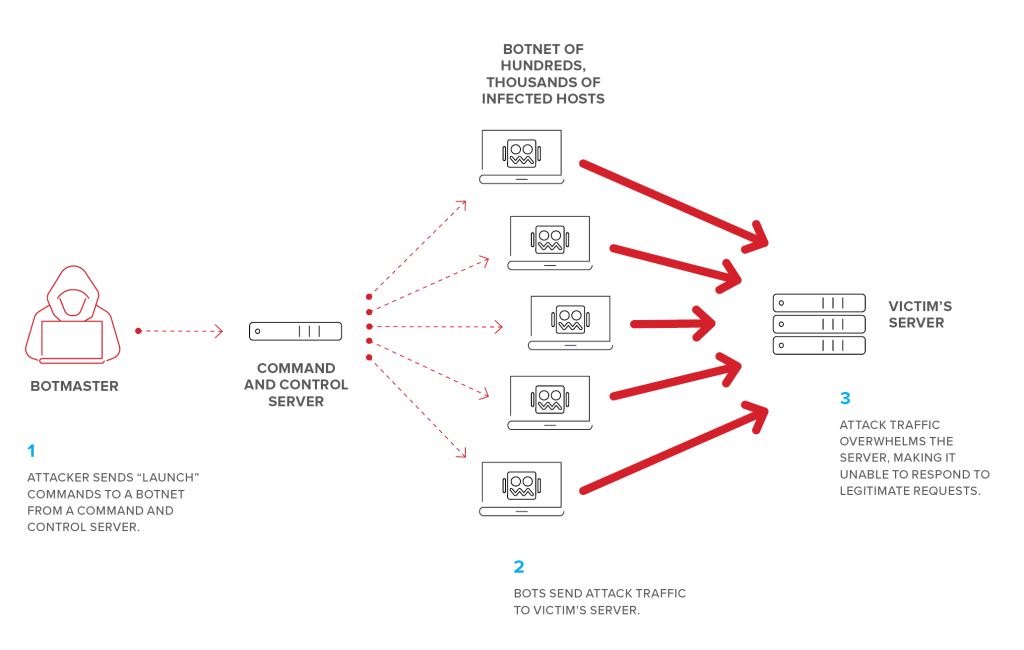
IoT devices are more susceptible to Denial-of-Service(DoS) attacks. In a firmware attack, the attacker may use vulnerabilities to replace a device’s basic software (usually its operating system) with a corrupted or defective version of the software, rendering it useless. This process, when done legitimately, is known as flashing, and its illegitimate counterpart is known as “phlashing”. When a device is phlashed, the owner of the device has no choice but to flash the device with a clean copy of the OS and any content that might’ve been put on the device. In a particularly powerful attack, the corrupted software could overwork the hardware of the device such that recovery is impossible without replacing parts of the device. The attacks on the device’s power system, though less popular, are possibly even more devastating.

Another kind of common attack is recruiting devices to create botnets and launch Distributed Denial of Service (DDoS) attacks. A denial of service (DoS) attack is characterized by an orchestrated effort to prevent the legitimate use of a service. DDoS attacks aim to overwhelm the infrastructure of the target service and disrupt normal data flow. DDoS attacks generally go through a few phases: recruitment, in which the attacker scans for vulnerable machines to be used in the DDoS attack against the target; exploitation and infection, in which the vulnerable machines are exploited, and malicious code is injected; communication, in which the attacker assesses the infected machines, sees which are online and decides when to schedule attacks or upgrade the machines; and attack, in which the attacker commands the infected machines to send malicious packets to the target.
IoT devices have become part of our daily. It has increased productivity and reduced human labor. But every IoT device comes with its own vulnerabilities and it’s our responsibility to safeguard them. These vulnerabilities could be addressed by Artificial Intelligence and Machine learning models. Stay tuned for the next blog on how AI is used to patch these vulnerabilities……….
*ARP (Address Resolution Protocol) spoofs the physical address ie the MAC address within the same network segment. *DNS (Domain Name System) spoofs IP addresses of legitimate sites and its effect can spread across multiple networks. *SSL (Secure Socket Layer) uses port number 443, encrypting data exchanged between the browser and the server and authenticating the user. So when the communication between the web browser and the server needs to be secured, the browser automatically switches to SSL as long as the server has an SSL certificate installed.
-Sruthi Sivaraman

Leave a comment